View the other posts in the series:
What we learned from Migrating custom applications to the Cloud
Part One Key Learnings Overview
Part Two Discover and Assess
Part Three Plan and Migrate
Part Four Monitor and Report
Since 2010, UnifyCloud has been helping customers migrate custom built, line-of-business (LoB) applications to the Cloud (PaaS, IaaS and SaaS)1. In this series we will share our key learnings, as well as best practices from our experiences of migrating custom built LoB applications to the Cloud. First, a quick review of why people are moving to the Cloud, and their concerns:
- 70% of CIOs are following a Cloud-first strategy as of 20162
- Key drivers for the migration to the Cloud: first is reducing costs, second is improving business agility.3
- Primary concerns around moving to the Cloud include Cybersecurity, Privacy and Compliance.4
The key to a successful Cloud migration is to develop a data-driven Cloud strategy. Develop a detailed understanding of your existing infrastructure, and use that as the starting point for developing your Cloud strategy. Once you have developed your strategy, create a detailed plan. We recommend a three-step process for migration planning, as outlined below. In this final post on this series we will focus on the Monitor & Report phase.

Monitor & Report
Design your new applications with life cycle in mind by enforcing standard components and operational automation.5
What You Need to Know About Cloud Application Development, Gartner
There is no “once and done” with Cloud migration. Applications change, threats change, the regulatory environment changes, and the underlying Cloud Service Provider platforms change daily. We call this ‘drift’. Your Cloud applications are in a constant state of drift. To monitor drift, you should establish governance standards for Cost, Cybersecurity and Compliance (GRC). You will need to monitor and report against the governance standards across subscriptions as PaaS environments evolve, applications are changed, and enterprise standards are updated to address changing threat environments relative to the cybersecurity and compliance baselines.
We have found that a best practice is to collect all of an organizations Cybersecurity Guidance into a single knowledgebase, where it can be updated and kept current by Subject Matter Experts (SME). The recommendations are then published through tools that are used by developers. The Knowledgebase contains best practices, and are an effective way to share learnings across your organization. The tools should also provide a way for the organization to monitor and report on the subscriptions, to ensure that the cost controls, cybersecurity recommendations and regulatory guidance are being followed properly. Cybersecurity recommendations should be grouped into categories including, but not limited to:
- Functional Cybersecurity Recommendations
- Application Cybersecurity Control Recommendations
- Application Business Logic
- Configuration Settings
- Cybersecurity Information
- Input Validation
- Encryption
- Firewall
- Authentication
- Notice, Choice and Consent
CloudOrigin provides a knowledgebase that enables organizations to create baselines, and report on compliance across all Azure Services and configuration settings. This ensures your security standards as well as Governance and Regulatory Compliance (GRC) guidance (e.g. GDPR, SOX, PCI, etc.) are followed by all developers. For each service your SMEs can provide recommended best practices (e.g. baselines) that can then be reported against across one or all subscriptions.
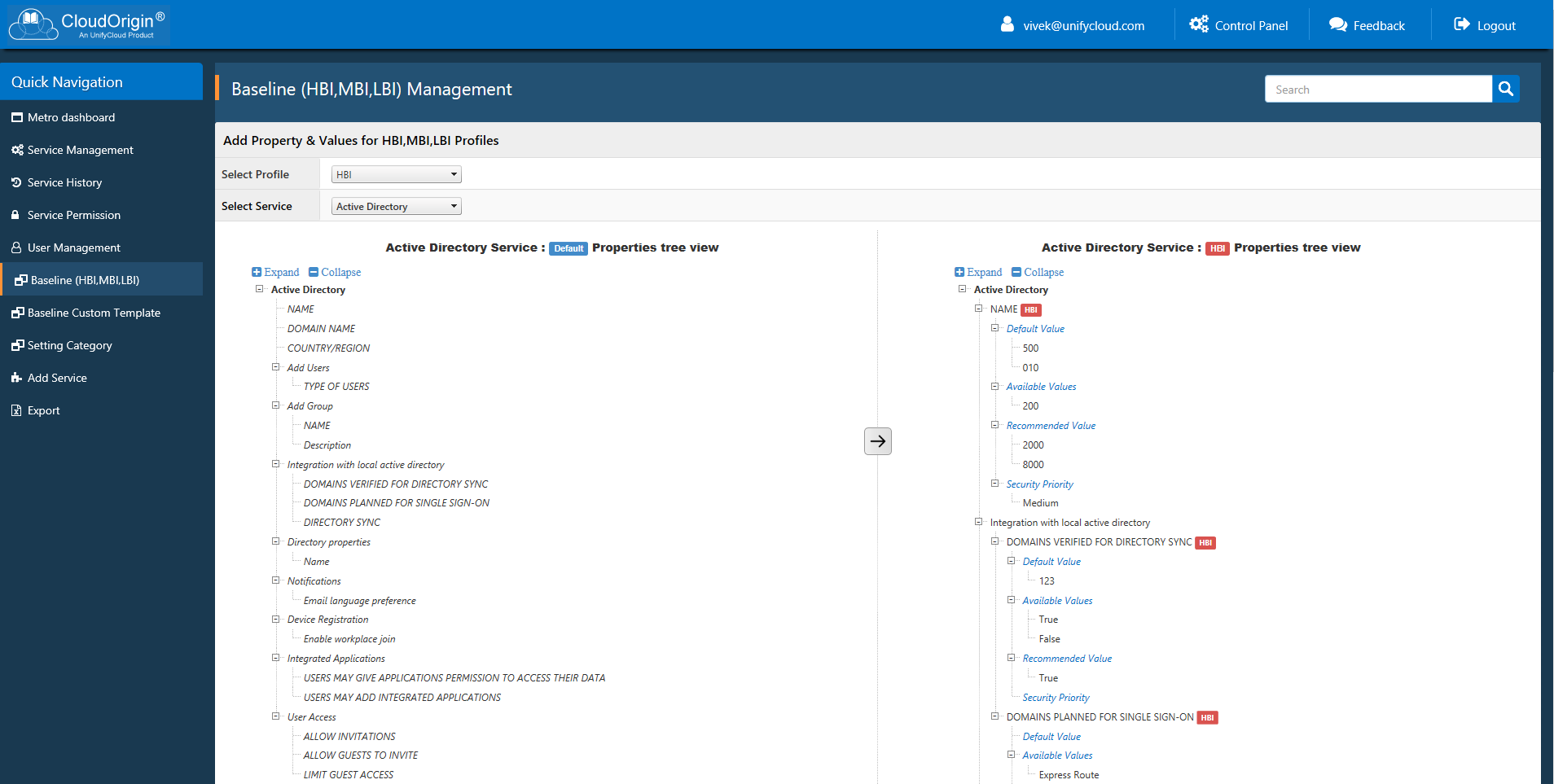
Compliance
For successful Cloud Migration you need to ensure your Governance and Regulatory Compliance (GRC) guidance (e.g. SOX, PCI, etc.) are followed by all developers. This ensures a developer will not inadvertently use an Azure service that is not compliant with a necessary regulatory framework while they are doing the migration, instead of finding out after the application has moved to Azure. The tools you use for scanning the application code should also identify the underlying services used and their compliance status with necessary regulations.
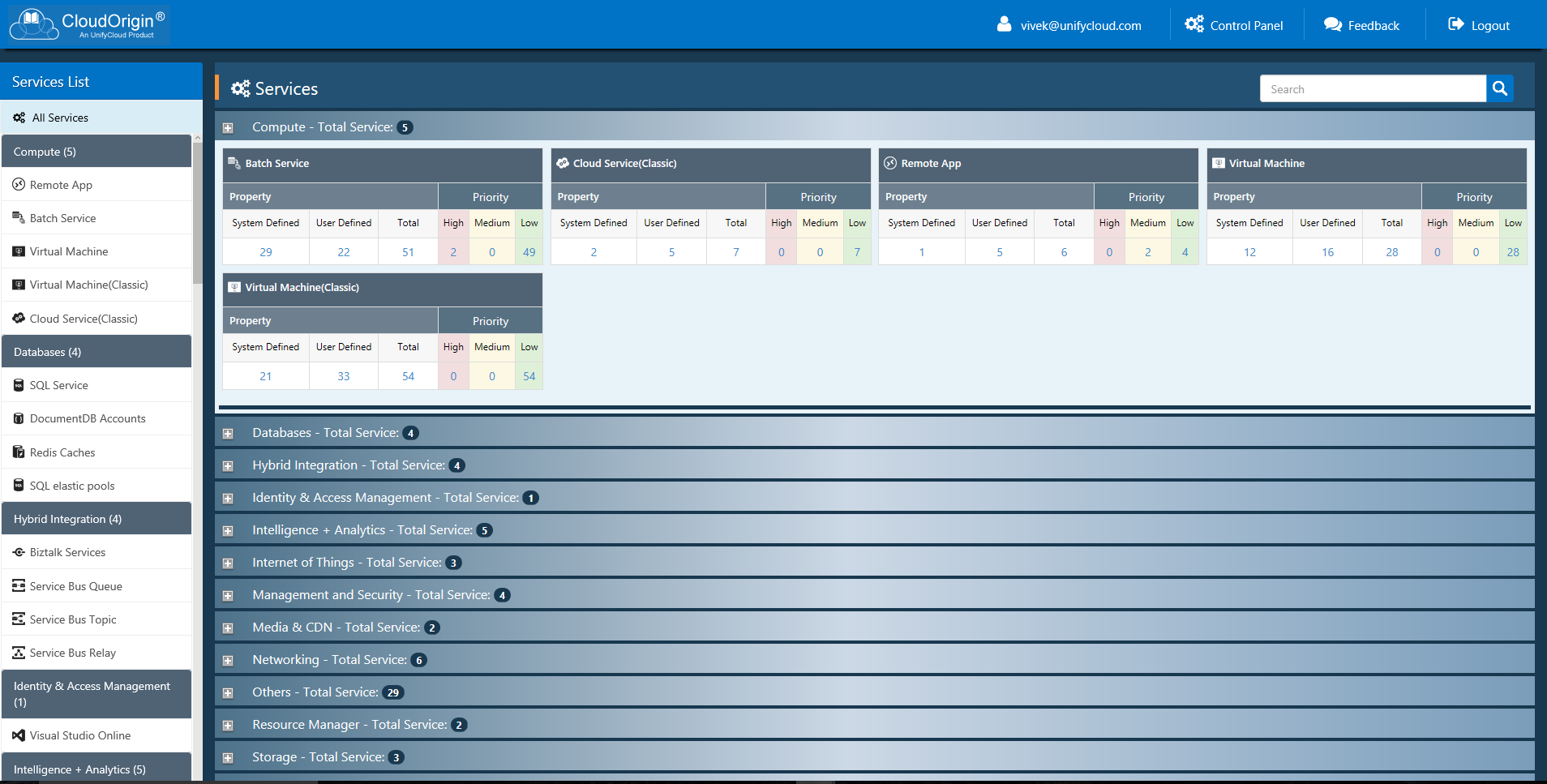
For example, we recently had a customer migrate an application to Azure that required SOC 2 Type 2 Compliance. The developer originally planned to use Azure Active Directory (AAD) Premium. After scanning the code for migration to PaaS, the compliance report stated that AAD Premium was not currently certified for SOC 2 Type 2. The developer was able to find out at the time of the initial code scan for migration, prior to doing any development work, that they would not be able to use AAD Premium. The developer could then seek an exception from their GRC team, or use an alternative solution.
Lesson #5: A CSP (e.g. AWS, Azure) may claim compliance with certain regulatory requirements. This does not necessarily mean that all the CSPs services are necessarily compliant with that regulatory requirement. Use tools to ensure each and every CSP service you use meets your regulatory requirements.
Developers need automated tools to be able to comply with Cybersecurity and GRC guidance during migration to Azure PaaS. Cybersecurity threats evolve Cloud platforms change at Cloud Speed, regulatory requirements change, and applications change. Developers are simply not able to keep up with these changes without support from automated tools. CloudPilot® provides real-time monitoring and alerts, pinpoints areas in the provisioned Cloud Services where settings have changed, and recommends any code level changes required.
Tooling needed to Monitor at Cloud Speed and Cloud Scale
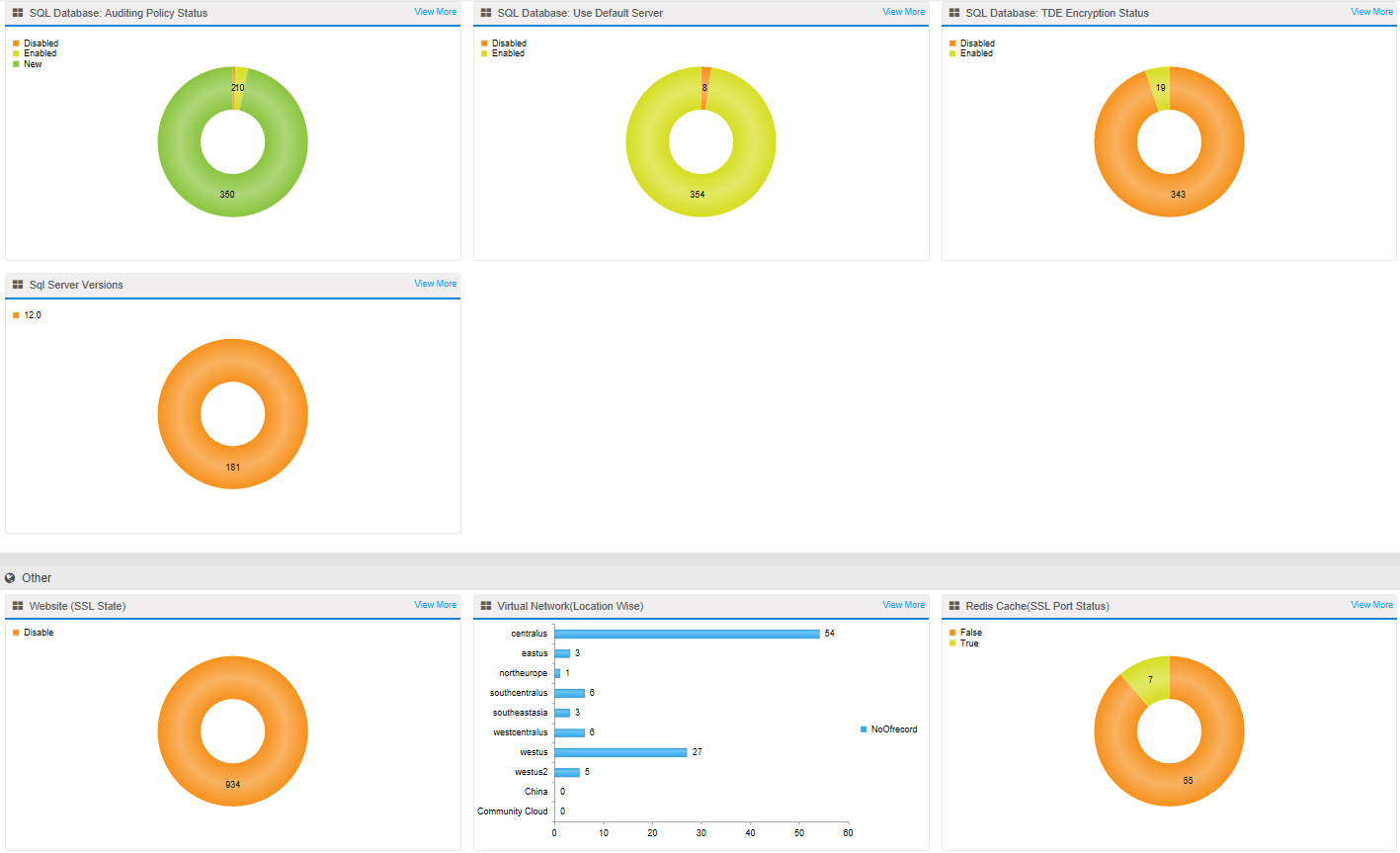
Subscription owners need a way to monitor and report applications running in the Cloud, for Cost Control, Cybersecurity, and Compliance (GRC). CloudSupervisor® provides real-time monitoring and alerts, pinpoints areas in the provisioned Cloud Services where settings have changed, and recommends any changes required for Cost Control, Cybersecurity, and Compliance (GRC) for Azure PaaS, IaaS, and Stack. CloudSupervisor provides dashboards for Cost Control, Cybersecurity, and Compliance:
- Action oriented personalized dashboards
- Coverage for PaaS and IaaS down to resource level
- Daily data refresh
- Snoozing
- Exception flow
- Customizable Alerts
- Dashboards available on Organization level
Cost
CloudSupervisor provides organizations with detailed visibility into their spending across all Azure services, and VMs. Dashboards provide drill down reports for individual subscription owners, or across the organization, for an all up view of Cloud spend. Rightsizing Azure VMs, Resources, and Services such as SQL Azure, identifies ‘cold’ and ‘hot’ Azure resources. ‘Cold’ resources can release unused Azure Compute, Storage, Network, or Database services to reduce costs. ‘Hot’ resources may be scaled up improve performance and responsiveness. Budgets can be easily set for individuals and organizations, for standard timeframes or custom date ranges, with alert notifications. CloudSupervisor subscription owners with detailed recommendations on rightsizing Services and VMs to achieve Cloud savings, enabling customers to routinely save 30-40% of their Azure spend.
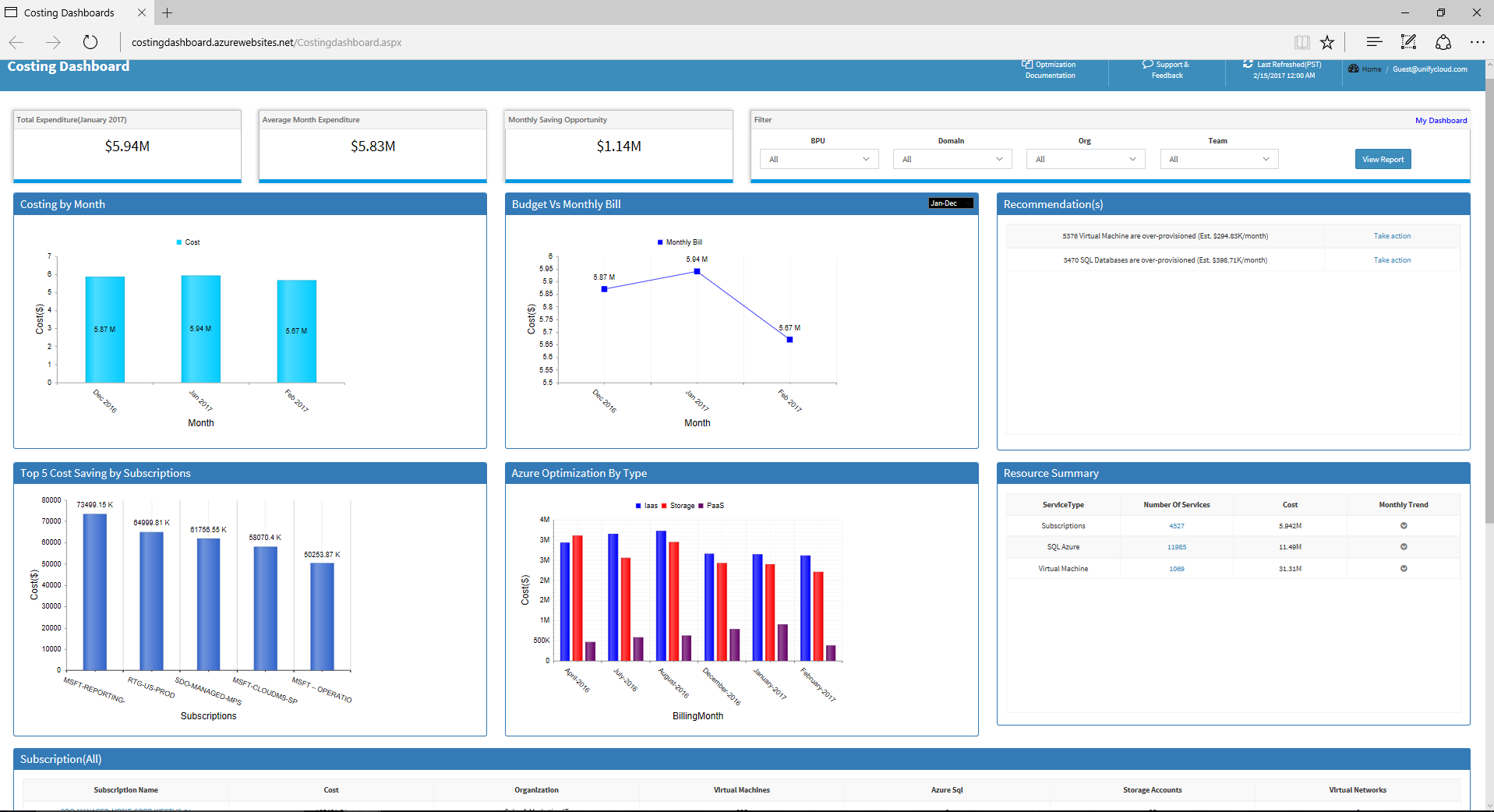
Cybersecurity & Compliance
Given the continuous changes in the Cybersecurity threat landscape, the daily changes in Cloud platforms by CSPs, changes to regulatory requirements, and changes to the applications themselves, application developers will struggle to maintain best practices in cost control, cybersecurity, and compliance. For developers to be successful at Cloud Speed and Cloud Scale, they need support from automation and tools.
CloudSupervisor® keeps application owners alerted to how their applications remain in compliance with the security baselines and internal controls configured for applications running on Azure. Baseline configuration based on GRC such as SOX, GDPR, HBI, MBI, & LBI, and compare to Baselines with alerts & detailed reporting. Reporting capabilities include:
- Action oriented personalized security dashboard
- Coverage for PaaS and IaaS resources.
- Daily data refresh
- Compliance exception flow
- Reporting available using Organization level (e.g. VP, Director, individual, etc.)
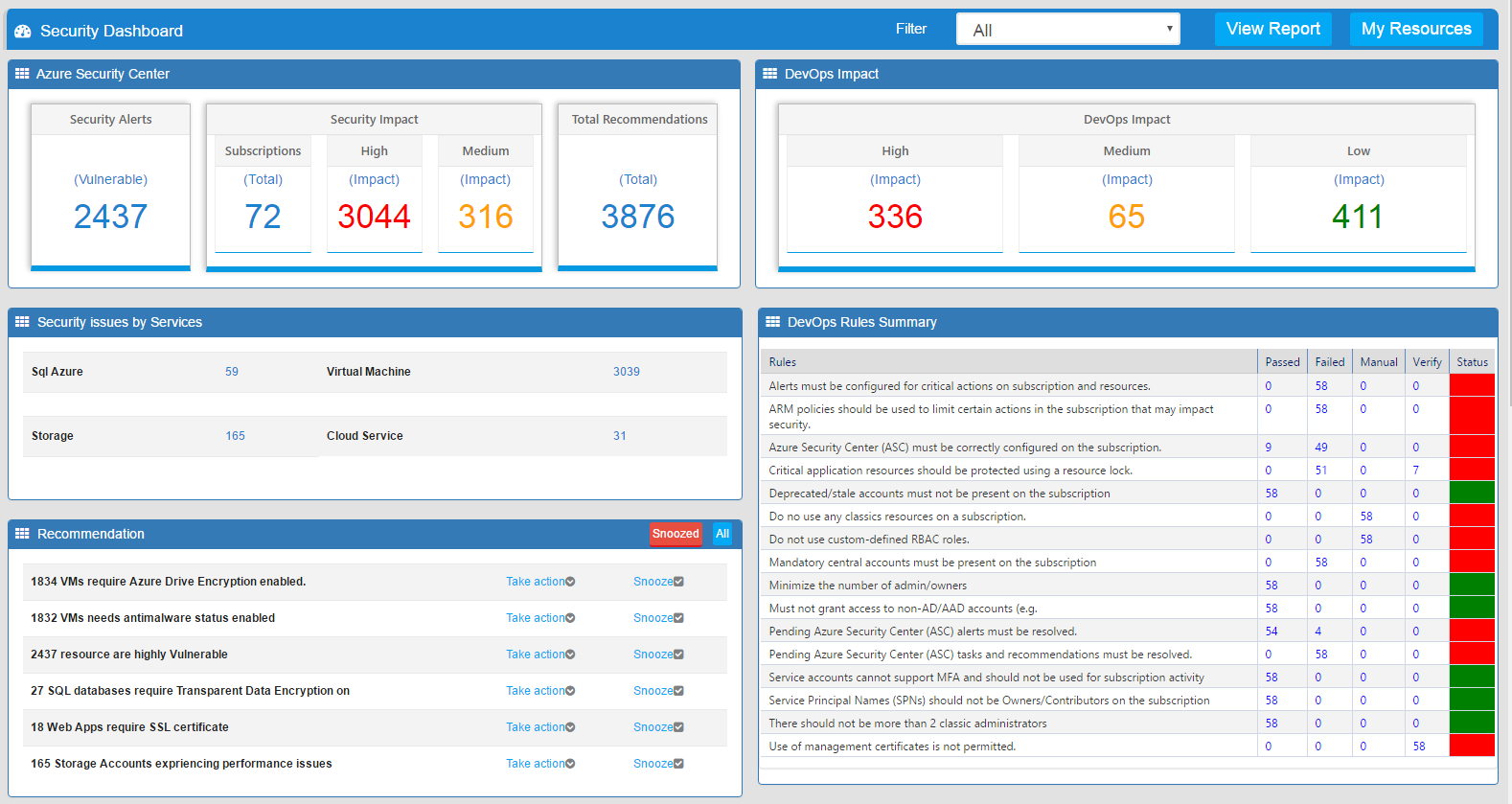
CloudSupervisor allows alerts to be customized for any of the Azure services configuration setting to report on how applications remain in compliance with the security baselines and internal controls configured in CloudOrigin. Individual dashboards as well as management dashboards (up to CVP) can be created and monitored.
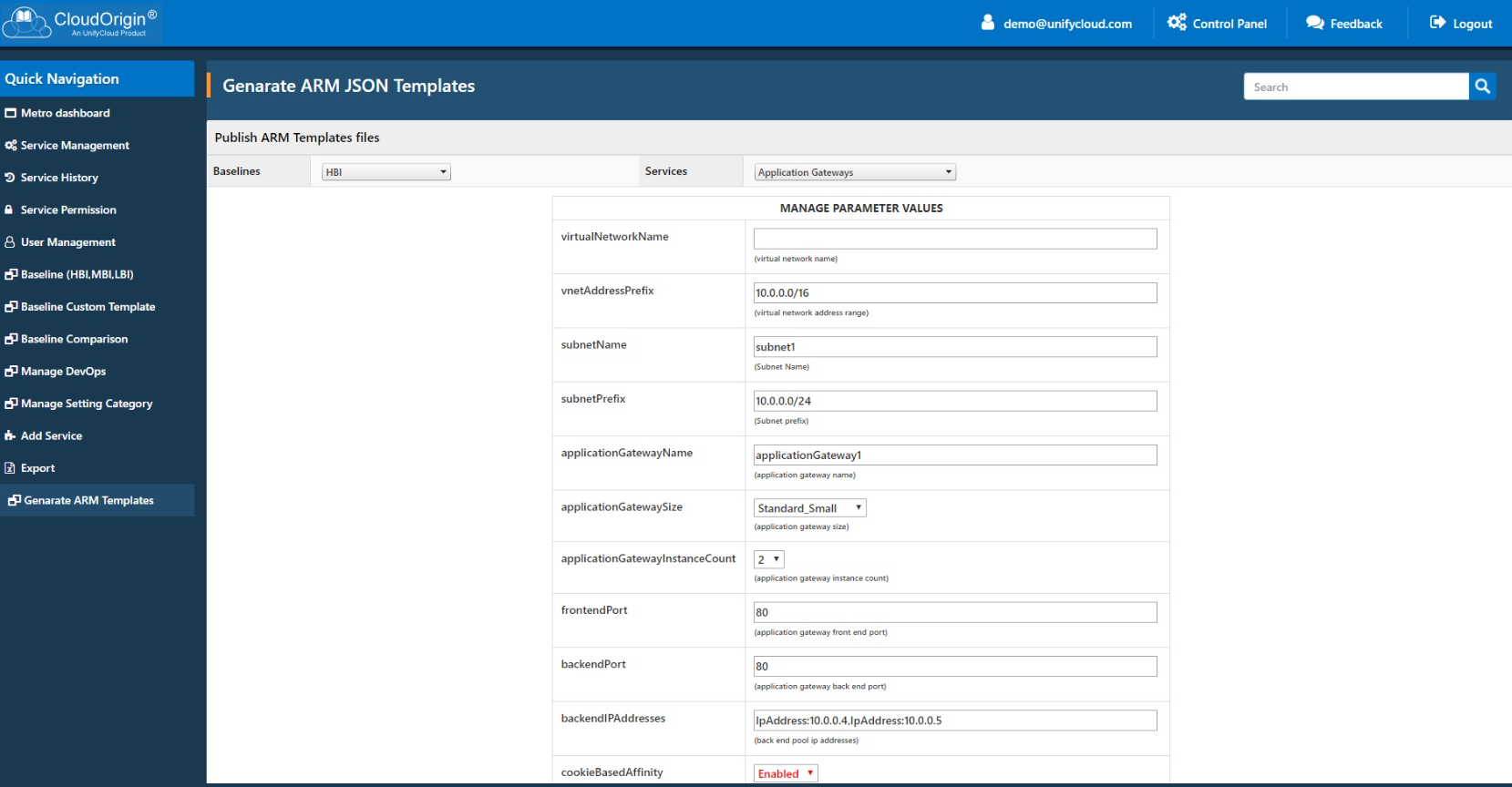
CloudOrigin is a customizable knowledgebase of all Azure services settings and configurations, recommended code changes, guidance, etc., for enterprises to define to establish their GRC standards. It is the knowledge repository that informs the suite of CloudAtlas® tools. With feature level changes rapidly in Azure to enhance capabilities and performance, CloudOrigin ensures that at the point of deployment, as well as during ongoing operations, Cloud-based applications remain in compliance with company standards. The CloudOrigin knowledgebase is updated monthly to stay current with all the latest changes to Azure, as new services are added, other services deprecated, and new settings become available. Customers and SIs can create baselines to ensure cybersecurity and compliance for applications, such as GDPR, SOX, PCI. The CloudOrigin recommendation engine can be customized to drive best practices for Cybersecurity, GRC, and Cost control.
The Cloud requires scalable solutions that can monitor and report on individual subscriptions, and across the enterprise, as well as provide alerts when any Cloud Service settings or controls have drifted from the baseline settings. Effective monitoring of applications in the Cloud is a key component of staying secure and compliant. The Subscription owner and the CIO need visibility into the applications down to the application code level to protect against drift, ensuring that applications remain visible and compliant with the Enterprise’s cybersecurity policy, to manage and control risk from applications in the Cloud.
Lesson #6: Migrating to the Cloud is a journey, not a destination. There is no ‘once and done’ when you move to the Cloud.
Code Submission Process
An organization should follow one of two processes to ensure developers follow and adhere to best practices. One option is when developers submit the application code for deployment to the Cloud, they should provide attestation that the application meets all the organizations Cybersecurity and GRC requirements, and include the report that supports this claim. The second option is to have a team review and scan all applications before they migrate them to the Cloud to ensure Cybersecurity and Compliance requirements are met. Whichever option is selected, once applications are in the Cloud, they are continuously monitored to ensure they follow cost, cybersecurity and GRC best practices.
Conclusion:
The five lessons we have learned around successful Cloud Migrations include:
Lesson #1: Tools and processes designed for on premise migrations every 3-5 years do not work at Cloud Speed and Cloud Scale. You will need integrated, automated, data driven tools to ensure you control your costs, maintain cybersecurity standards, and uphold GRC thru each step of the Cloud Migration process.
Lesson #2: Use a data-driven tool to produce the Cloud Readiness Assessment, which will drive your Cloud Strategy, providing you with a detailed roadmap for your journey to the Cloud.
Lesson #3: Simple ‘Lift and Shift’ to the Cloud is not optimal. Modernize your applications for PaaS, or size the Cloud VMs based on your historical usage as the starting point.
Lesson #4: To support migrations at Cloud Speed and Cloud Scale, you need to use automated tools. The tools must scan applications for migration to PaaS and IaaS in minutes instead of the months it would take to do so manually, identifying application dependencies, and providing recommendations for cost control, cybersecurity, compliance.
Lesson #5: A CSP (e.g. AWS, Azure) may claim compliance with certain regulatory requirements. This does not necessarily mean that all the CSPs services are necessarily compliant with that regulatory requirement. Use tools to ensure each and every CSP service you use meets your regulatory requirements.
Lesson #6: Migrating to the Cloud is a journey, not a destination. There is no ‘once and done’ when you move to the Cloud.
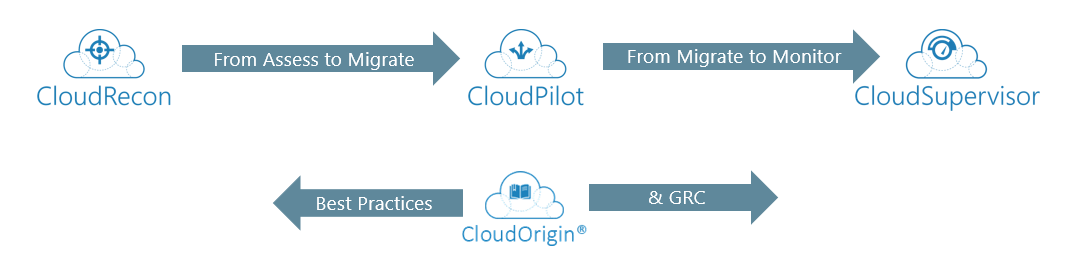
Successful migrations to the Cloud require being data driven, and following a structured process. Our experience recommends using integrated automated tools for enterprises to manage the complexity of migrating application to the Cloud, through their application lifecycles, at Cloud Speed and Cloud Scale. Different Tools are used at different stages of the process. CloudAtlas looks at migration process and challenges holistically to support Cloud migration and applications, with an underlying knowledgebase to ensure best practices are followed throughout the entire process. The CloudAtlas suite of solutions, are available individually or as a bundle via SaaS. For more information, please go to www.Cloudatlasinc.com.

References
1 NIST Reference to Cloud Service Models starts on page 2: http://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-145.pdf
2 IDC CIO Agenda webinar
3 InformationWeek; September 29, 2016 & Seth Robinson; Senior Director, CompTIA
4 SIM IT Trends Study, 2017
5 Gartner: What You Need to Know About Cloud Application Development, November, 2013 G00247030
View the other posts in the series:
What we learned from Migrating custom applications to the Cloud
Part One Key Learnings Overview
Part Two Discover and Assess
Part Three Plan and Migrate
Part Four Monitor and Report


